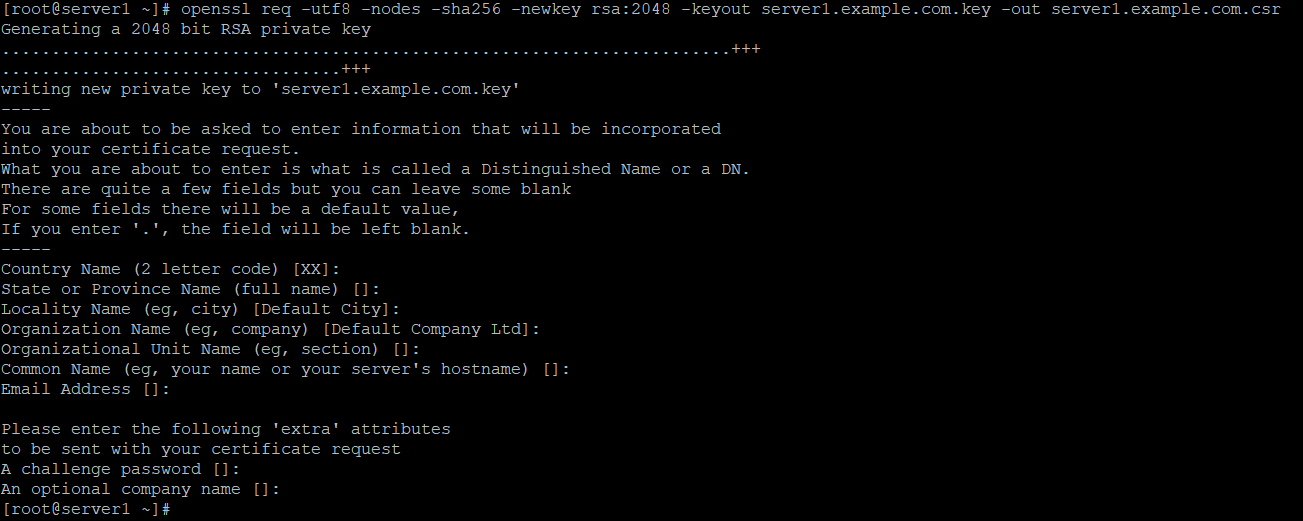
SiteGround uses key pairs for SSH authentication purposes, as opposed to plain username and password. More information on SSH keys is available here. You can generate an SSH key pair in Mac OS following these steps. Mac OS X also ships with OpenSSL pre-installed. For Windows a Win32 OpenSSL installer is available. Remember, it’s important you keep your Private Key secured; be sure to limit who and what has access to these keys. Converting PEM encoded certificate to DER openssl x509 -outform der -in certificate.pem -out certificate.der. Create a new key. Openssl genpkey -algorithm RSA -pkeyopt rsakeygenbits:2048 -out store.scriptech.io.key.pem. Create a new CSR. Openssl req -new -sha256 -key store.scriptech.io.key.pem -config /etc/ssl/openssl.cnf -out store.scriptech.io.csr Verify the CSR. To view the contents of your new CSR, use the following command.
- Create a hashed MAC using 'key'. Create MAC (keyed Message Authentication Code). The most popular MAC algorithm is HMAC (hash-based MAC), but there are other MAC algorithms which are not based on hash, for instance gost-mac algorithm, supported by ccgost engine. MAC keys and other options should be set via -macopt parameter.
- Openssl pkcs12 -export -clcerts -inkey private.key -in certificate.crt -out MyPKCS12.p12 -name 'Your Name' where private.key is your existing private RSA key, certificate.crt is your existing certificate and MyPKCS12.p12 is the name of the file to create. This file can then be imported into your keychain.
SYNOPSIS
openssldgst [-Idigest] [
openssl Idigest [...]
DESCRIPTION
The digest functions output the message digest of a supplied file or files in hexadecimal. The digest functions also generate and verify digital signatures using message digests.
The generic name, dgst, may be used with an option specifying the algorithm to be used. The default digest is sha256. A supported digest name may also be used as the command name. To see the list of supported algorithms, use the openssl_list--digest-commands command.
Options
Print out a usage message.
Specifies name of a supported digest to be used. To see the list of supported digests, use the command openssl_list--digest-commands.
prints out the digest in two digit groups separated by colons, only relevant if hex format output is used.
prints out BIO debugging information.
outputs digest as a hex dump. This is the default case for a 'normal' digest as opposed to a digital signature. See NOTES below for digital signatures using
outputs the digest or signature in binary form.
output the digest in the 'coreutils' format used by programs like sha1sum.
specifies the file name to output to, or standard output by default.
digitally signs the digest using the private key in filename.
Specifies the key format to sign digest with. The DER, PEM, P12, and ENGINE formats are supported.
Pass options to the signature algorithm during sign or verify operations. Names and values of these options are algorithm-specific.
the private key password source. For more information about the format of arg see the PASS PHRASE ARGUMENTS section in openssl.
verifies the signature using the public key in filename. The output is either Verification OK or Verification Failure.
verifies the signature using the private key in filename.
specifies the actual signature to verify.
create a hashed MAC using 'key'.
create MAC (keyed Message Authentication Code). The most popular MAC algorithm is HMAC (hash-based MAC), but there are other MAC algorithms which are not based on hash, for instance gost-mac algorithm, supported by ccgost engine. MAC keys and other options should be set via
Passes options to MAC algorithm, specified by
Specifies MAC key as alphanumeric string (use if key contain printable characters only). String length must conform to any restrictions of the MAC algorithm for example exactly 32 chars for gost-mac.
Specifies MAC key in hexadecimal form (two hex digits per byte). Key length must conform to any restrictions of the MAC algorithm for example exactly 32 chars for gost-mac.
specifies a file or files containing random data used to seed the random number generator. Multiple files can be specified separated by an OS-dependent character. The separator is ; for MS-Windows, , for OpenVMS, and : for all others.

Writes random data to the specified file upon exit. This can be used with a subsequent
compute HMAC using a specific key for certain OpenSSL-FIPS operations.
Use engine id for operations (including private key storage). This engine is not used as source for digest algorithms, unless it is also specified in the configuration file or
When used with the
specifies the file or files to digest. If no files are specified then standard input is used.
EXAMPLES
To create a hex-encoded message digest of a file:
To sign a file using SHA-256 with binary file output:
To verify a signature:
NOTES
The digest mechanisms that are available will depend on the options used when building OpenSSL. The openssl_listdigest-commands command can be used to list them.
New or agile applications should use probably use SHA-256. Other digests, particularly SHA-1 and MD5, are still widely used for interoperating with existing formats and protocols.
When signing a file, dgst will automatically determine the algorithm (RSA, ECC, etc) to use for signing based on the private key's ASN.1 info. When verifying signatures, it only handles the RSA, DSA, or ECDSA signature itself, not the related data to identify the signer and algorithm used in formats such as x.509, CMS, and S/MIME.
A source of random numbers is required for certain signing algorithms, in particular ECDSA and DSA.
The signing and verify options should only be used if a single file is being signed or verified.
Hex signatures cannot be verified using openssl. Instead, use 'xxd -r' or similar program to transform the hex signature into a binary signature prior to verification.
Openssl Create Key Pair
HISTORY
The default digest was changed from MD5 to SHA256 in OpenSSL 1.1.0. The FIPS-related options were removed in OpenSSL 1.1.0.
COPYRIGHT
Copyright 2000-2019 The OpenSSL Project Authors. All Rights Reserved.
Licensed under the OpenSSL license (the 'License'). You may not use this file except in compliance with the License. You can obtain a copy in the file LICENSE in the source distribution or here: OpenSSL.
Using Openssl To Create Keys For Mac Osx
AVAILABILITY
PTC MKS Toolkit for System Administrators
PTC MKS Toolkit for Developers
PTC MKS Toolkit for Interoperability
PTC MKS Toolkit for Professional Developers
PTC MKS Toolkit for Professional Developers 64-Bit Edition
PTC MKS Toolkit for Enterprise Developers
PTC MKS Toolkit for Enterprise Developers 64-Bit Edition
PTC MKS Toolkit 10.3 Documentation Build 39.
Download and install the OpenSSL runtimes. If you are running Windows, grab the Cygwin package.
OpenSSL can generate several kinds of public/private keypairs.RSA is the most common kind of keypair generation.[1]
Other popular ways of generating RSA public key / private key pairs include PuTTYgen and ssh-keygen.[2][3]
Generate an RSA keypair with a 2048 bit private key[edit]
How To Use Openssl On Mac
Execute command: 'openssl genpkey -algorithm RSA -out private_key.pem -pkeyopt rsa_keygen_bits:2048'[4] (previously “openssl genrsa -out private_key.pem 2048”)
e.g.
Make sure to prevent other users from reading your key by executing chmod go-r private_key.pem afterward.
Extracting the public key from an RSA keypair[edit]
Execute command: 'openssl rsa -pubout -in private_key.pem -out public_key.pem'
e.g.
A new file is created, public_key.pem, with the public key.
It is relatively easy to do some cryptographic calculations to calculate the public key from the prime1 and prime2 values in the public key file.However, OpenSSL has already pre-calculated the public key and stored it in the private key file.So this command doesn't actually do any cryptographic calculation -- it merely copies the public key bytes out of the file and writes the Base64 PEM encoded version of those bytes into the output public key file.[5]
Viewing the key elements[edit]
Execute command: 'openssl rsa -text -in private_key.pem'

All parts of private_key.pem are printed to the screen. This includes the modulus (also referred to as public key and n), public exponent (also referred to as e and exponent; default value is 0x010001), private exponent, and primes used to create keys (prime1, also called p, and prime2, also called q), a few other variables used to perform RSA operations faster, and the Base64 PEM encoded version of all that data.[6](The Base64 PEM encoded version of all that data is identical to the private_key.pem file).
Password-less login[edit]
Often a person will set up an automated backup process that periodically backs up all the content on one 'working' computer onto some other 'backup' computer.
Because that person wants this process to run every night, even if no human is anywhere near either one of these computers, using a 'password-protected' private key won't work -- that person wants the backup to proceed right away, not wait until some human walks by and types in the password to unlock the private key.Many of these people generate 'a private key with no password'.[7]Some of these people, instead, generate a private key with a password,and then somehow type in that password to 'unlock' the private key every time the server reboots so that automated toolscan make use of the password-protected keys.[8][3]
Further reading[edit]
- ↑Key Generation
- ↑Michael Stahnke.'Pro OpenSSH'.p. 247.
- ↑ ab'SourceForge.net Documentation: SSH Key Overview'
- ↑'genpkey(1) - Linux man page'
- ↑'Public – Private key encryption using OpenSSL'
- ↑'OpenSSL 1024 bit RSA Private Key Breakdown'
- ↑'DreamHost: Personal Backup'.
- ↑Troy Johnson.'Using Rsync and SSH: Keys, Validating, and Automation'.
- Internet_Technologies/SSH describes how to use 'ssh-keygen' and 'ssh-copy-id' on your local machine so you can quickly and securely ssh from your local machine to a remote host.
